|
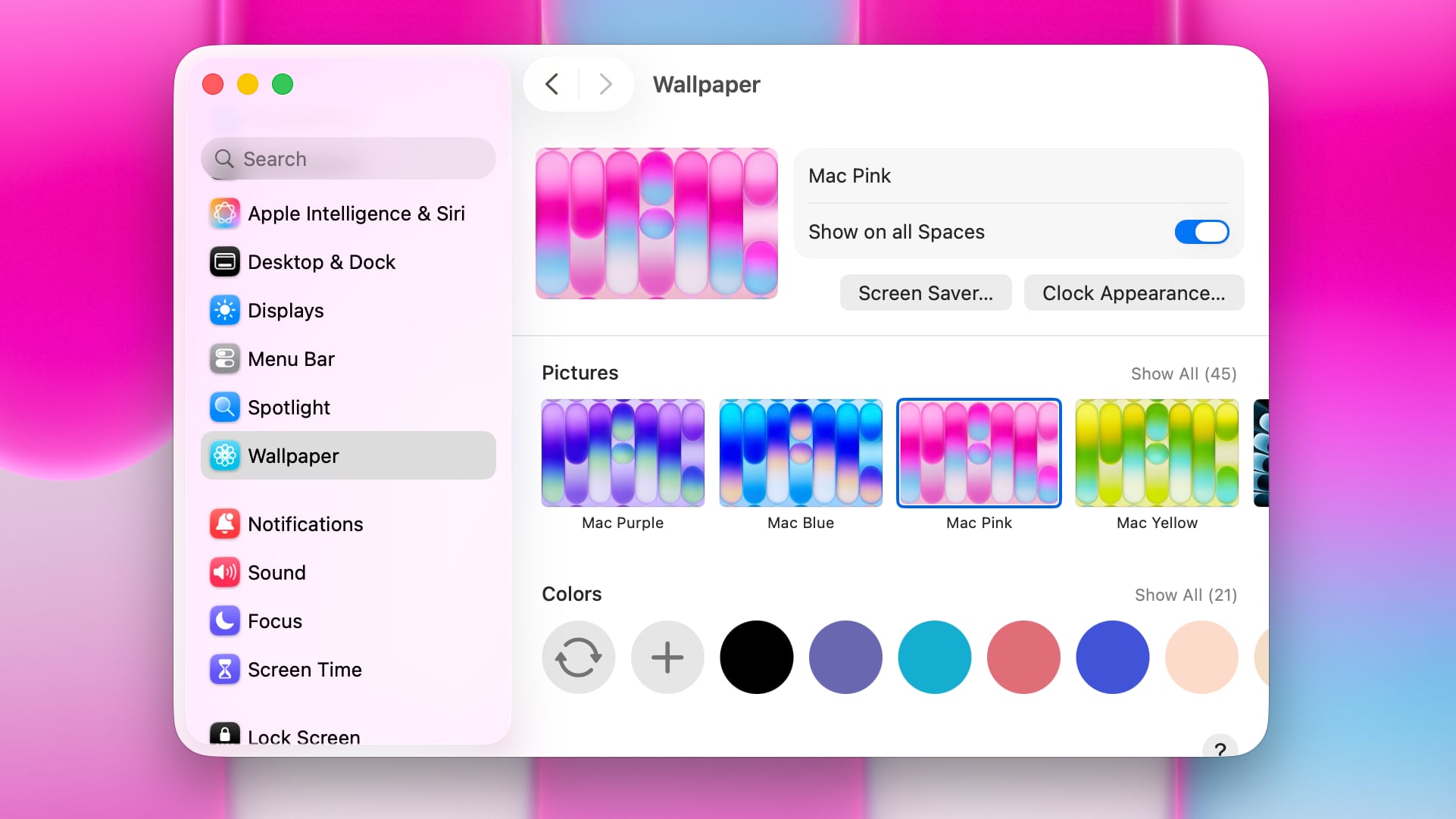 The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today. The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today.
|
|
Mark Gurman at Bloomberg is back with the latest rumors about what's afoot with Apple's future plans, and how its ongoing difficulties with artificial intelligence seem to be creating further delays for its next wave of product launches. His sources say that Apple is expected to postpone the debut of its smart home display until later in 2026, likely September when it often introduces new gadgets. Although the hardware has reportedly been finished for months, this delay is being credited to the company's AI-centric overhaul of Siri still not being complete.
The device, internally known as J490, has been one of Apple's many poorly-kept secrets. Rumors about a HomePod smart speaker coupled with a screen first emerged back in 2022 and have resurfaced from time to time in the interim, often with promises that the device's arrival was imminent. The latest claims anticipated that the official announcement was coming this spring, possibly as soon as this month. However, appears to Apple once again be hamstrung by an AI strategy that has left
|
|
 Apple today seeded the fourth betas of upcoming iOS 26.4 and iPadOS 26.4 updates to developers for testing purposes, with the software coming a week after Apple provided the third betas to developers. Apple today seeded the fourth betas of upcoming iOS 26.4 and iPadOS 26.4 updates to developers for testing purposes, with the software coming a week after Apple provided the third betas to developers.
|
|
Epic Games' courtroom battle with Google is over, but it's reportedly going to affect how its CEO can speak about the tech giant for years for years to come. According to The Verge, part of the settlement terms Epic had signed has a clause stating that Epic and Sweeney will have to speak positively about Google's competitiveness and app store operations going forward. "Epic believes that the Google and Android platform, with the changes in this term sheet, are procompetitive and a model for app store / platform operations, and will make good faith efforts to advocate for the same," the clause reportedly reads.
Further, The Verge says the settlement terms between the companies will expire five years after Google is done rolling out changes to its service fees. Since Google expects to finish implementing changes worldwide by September 30, 2027, Sweeney can't speak negatively about the company until after September 30, 2032.
Sweeney is one of the most vocal critic of how Apple and Google operate their app stores, which had led to several lawsuits between the companies. He once called both Apple and Google "gangster-style businesses" that will "always continue" to be engaged in illegal practices and just pay the fine afterwards. Epic Games filed a lawsuit against Google in 2020, accusing it of illegal monopoly on app distribution and in-app billing services for Android devices. In 2023, Google lost the law
|
|
